A “Bombe” early computer, used to break the German Enigma code
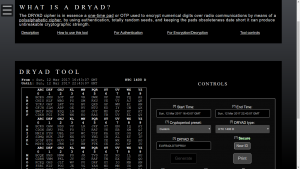
After I released the DRYAD generator, I received few reports that it would generate the same output every time. This is not good, even for training. Work, family, and life put my programming efforts on the back burner for a while. When I finally got back to it, I discovered that I committed an amateur programming mistake.
I forgot to seed the random generator
Computers are “deterministic” machines. That means that every action has a predictable action, or that the actions are “determined” by the programming. That is a good thing because computers would not be very useful if their output changed at random. However for generating cryptographic materials you need good randomness. In order to create the appearance of randomness computers use a “Pseudo Random Number Generator” (PRNG). A PRNG basically takes a number as input called the “seed”, and then runs it through a complicated series of mathematical equations that gives you a result that seems random, with no correlation to the input seed. For example, a seed of “1” might yield a result of “72542” while a seed of “2” might result in “17”.
My DRYAD bug
I forgot to add a line defining a seed, so most likely it would default to “0”
Every
Single
Time
resulting in the same DRYAD page being generated every time the program was run.
The Seed is the key
In order to get pseudo randomness that does not repeat, many programming classes teach using a value of time as the random seed. Computers keep time by counting the number of seconds since some predetermined date/time reference (called an “epoch”)
Since real time does not repeat I.E. it will only be 12:01 PM on January the 1st, 2017 once, using it as a seed guarantees that our seed is never repeated.
This is what I have added to the 1.01 version of the DRYAD generator.
Link HERE!
While it is pseudo random, it is still not good enough
While this is unpredictable enough for video games and entertainment, it sucks for real cryptography. For a single line on a DRYAD sheet, there are 403,291,461,126,605,635,584,000,000 possible combinations. That is over 403 Septillion combinations. However there are only just over 35 million seconds in a year. If you know the formula a given crypto uses, and you know it uses “time” as the seed, then you can run the formula and simply increment the seed, starting at the earliest possible time the computer was used. A modern computer can test years of “time” based seed in a few minutes, leaving a searchable database of every possible DRYAD sheet that could be generated in a given year. Not very secure by a determined adversary.
This is why the current version of the DRYAD generator should be limited to training purposes ONLY!
I hope to have an improved version later that will solve the “seed” problem.
An ideal crypto-secure seed would come from a very large unpredictable source. Government grade high level crypto use special devices that use an “entropy” source.
“Entropy” is defined as “lack of order or predictability.”
Imagine a very sensitive thermometer that can accurately read to 1/1000 of a degree. If that thermometer is in a computer case, it will measure the fluctuations of temperature inside. The temperature is affected by ambient room temperature, how hard the CPU and graphics cards are running, fan speed, etc. The temperature can fluctuate by as much as twenty degrees. twenty degrees doesn’t sound like a lot, a fluctuation between 100.0001 and 100.9999 degrees overs a much larger range of unpredictability.
Government certified entropy devices have been designed AND tested to insure that they are truly entropic (unpredictable) and evenly distributed. (if they generate a number between 1 and 10, a sample of a million tests should have roughly equal quantities of each value.)
Because of the value of entropic seeds in generating random numbers for cryptography, most modern computer operating systems now have “entropy pools” to be used in seeding PRNGs. These entropy pools combine mouse movements, keyboard timings, temperatures, hard drive seek times, and other unpredictable sources to populate the pool.
The next version of the DRYAD generator
I hope to include strong entropy and a better PRNG for the next version of the DRYAD generator. After that, I hope to add a GUI. I won’t put a timeframe on it, because if I do, life will guarantee that I won’t make the deadline.
P.S. The big numbers:
The number of possible combinations on a single DRYAD line:
403,291,461,126,605,635,584,000,000
aka 403.29 Septillion
The number of possible combinations for a full DRYAD sheet:
55,730,725,530,135,062,649,198,161,739,977,709,115,499,393,128,640,929,871,421,008,423,533,724,386,338,878,574,160,341,220,778,225,216,731,660,527,904,329,322,280,362,280,772,040,814,157,865,238,665,297,698,064,960,243,496,240,325,230,914,590,792,168,508,784,599,820,624,250,553,113,284,701,975,927,160,036,290,503,391,161,723,777,948,657,564,970,294,494,230,362,463,039,937,503,817,540,615,316,978,304,413,679,131,193,300,564,494,890,078,044,222,099,073,176,301,173,743,417,188,309,993,750,657,183,175,705,816,024,175,455,037,824,215,922,922,840,889,574,614,720,871,058,686,980,831,704,240,509,476,464,184,648,541,082,363,856,771,908,162,937,920,666,500,337,734,500,441,071,580,223,302,989,222,924,982,121,660,416,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000
I can not count that high.
Number of seconds in a year: (and possible time based random seeds for a given year)
31,536,000
aka 31.54 Million
Estimated age of the universe:
13.82 Billion years old
Number of Seconds in the universe so far:
About 484,000,000,000,000,000
aka 484 Quadrillion
aka orders of magnitude fewer seconds in the history of the universe, than possible combinations for a single line of a DRYAD sheet!